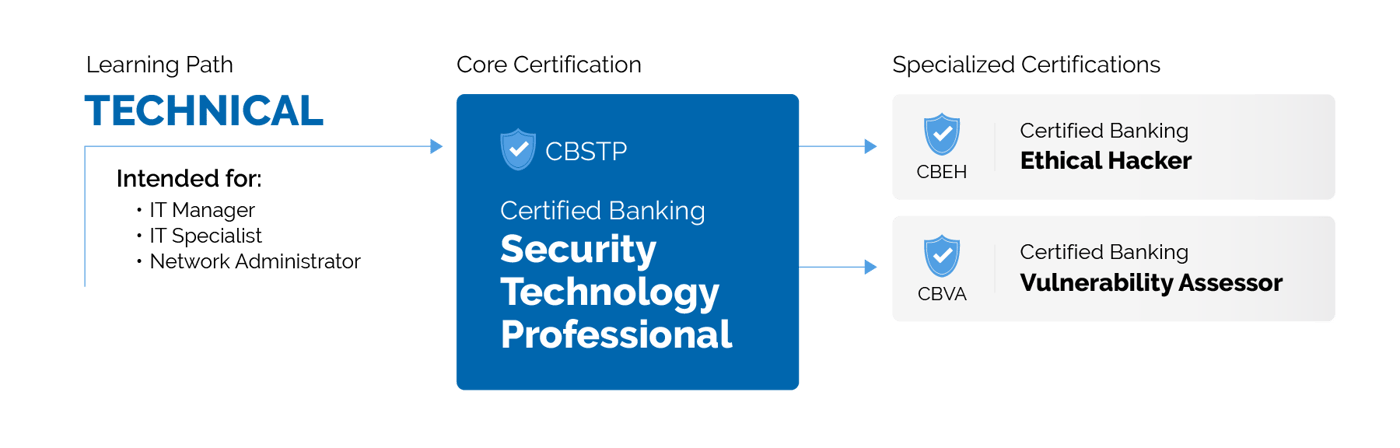
CBEH: Certified Banking Ethical Hacker

Description
This course will allow you to master the concepts and technologies used by today’s hackers to better defend your institution.
TOPICS:
- The four step process: information gathering, scanning, exploitation, and post exploitation
- How attackers leverage the web
- Post scanning, fingerprinting, and versioning techniques
- Vulnerability scanning with Nessus
- Exploitation and privilege escalation utilizing John the Ripper
- Exploitation with Metasploit
- Exploiting the human by “hacking” users
- Post exploitation and meterpreter
WHO SHOULD ATTEND:
- IT Manager, Network Administrator, IT Specialist
This course is self-paced with 10 weeks allowed to complete. Final exam is required to earn the certification.
By purchasing this certification, you are hereby agreeing to the policies and procedures of the SBS Institute. Click HERE to read and review.
CPE Credits
 |
SBS | 4.00 |
Learning Objectives
- Gain real-world cybersecurity defense knowledge and skills you can put to use immediately.
- Take security into your own hands with the ability to run scanning processes on demand as threats arise.
- Better understand your risks so you can communicate them to your team more effectively.
- Assist with the Cybersecurity Controls domain of the FFIEC Cybersecurity Assessment.
Content
| Module 1: Open Source Information Gathering | Module | ||
| Module 2: Open Source Information Gathering Part 2 | Module | ||
| Module 3: Scanning | Module | ||
| Module 4: Scanning Part 2 | Module | ||
| Module 5: Exploitation | Module | ||
| Module 6: Post-Exploitation | Module | ||
| Module 7: Password Exploitation | Module | ||
| Module 8: Social Engineering | Module | ||
| CBEH Final Exam | Module |
“I was fortunate enough to be involved in the first offering of the certification program and due to the program’s benefits, I continue to renew each year. Each year I learn something new and more innovative ways to grow the bank’s program. SBS has been a resource not only for their certification programs, but also as a security partner.”
- Rachel Losey, PA
- Rachel Losey, PA
Continue your cyber education by exploring the other courses available in the Technical Learning Path: